Michael Shea is the Managing Director of the Dingle Group and the Chair of Sovrin Foundation’s SSI in IoT Working Group. In this podcast we discussed the white paper he authored on Self Sovereign Identity and IoT. To explain the opportunities SSI can provide to IoT, Michael introduces us to three profiles: Jamie (machine to person), Bob (machine to machine) and Bessie the cow (digital twin).
What is blockchain?
Blockchain is a decentralised database, which is cryptographically secured and immutable. The decentralised part means that it operates in a wider ecosystem than traditional ones, that sits within corporate firewalls, which gives it greater resiliency and redundancy.
The cryptographic component along with the different proof of work, resolve the double spend problem and bring a level of assurance that transactions have not been modified.
An introduction to Self-Sovereign Identify (SSI), Decentralised Identifiers (DID) and verifiable credentials.
Self-sovereign identity is an identity model, where an entity is in control of its own identity and information related to it. SSI as a concept started to take shape in 2016 with Christopher Allen’s 10 principles of self-sovereign identity. In December 2020 the Sovrin Foundation released its 12 principles of self-sovereign identity, which fundamentally is about an entity’s ability to control the information about themselves.
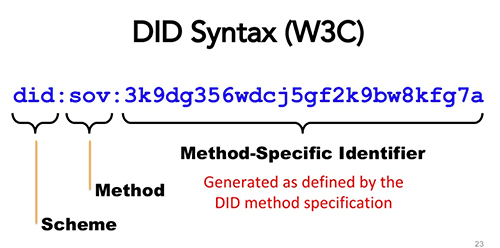
Decentralised identifiers (DIDs) is a pointer to the identify information known as a DID document that helps to create the trust layers within SSI.
A verifiable credential is a cryptographic bundle that is created by an issuer of a credential such as the DVLA for a driver’s license. That credential includes attributes stating that the driver is legally entitled to drive a vehicle and it may contain other pieces of information such as your address and other details. A cryptographic bundle is signed using the public private key of the issuer in this case the DVLA which is then returned to the holder of the driver’s license. That holder can then use that credential to a verifier to indicate his/her authorisation to drive a vehicle.
Internet of Things (IoT)
Machine to Person
Machine to person is where a device is interacting with an individual. The machine can be attached or worn by a person and is measuring some aspect of the person’s personal or physical environment and transmitting this data directly or indirectly to a connected device. For example, a person with diabetes would have a sensor that is attached to their body reading their glucose level and communicating the data to an app on a smartphone or a separate physical device.
Machine to machine
Machine to machine is the communication between an IoT device and a computer, smartphone or device. Using the above analogy, the machine is the device or the smartphone speaking up to a central repository for transmitting that information to an endocrinologist on behalf of the patient.
Digital twins
A digital twin is a virtual digital representation of a physical object. That can be a person, an animal, or a thing. The most common use of digital twins is in an industrial setting. For example, a jet engine has hundreds of sensors embedded inside it, streaming data off to the aircraft engine manufacturers and creating a whole digital profile of itself.
Risks associated with IoT
On the 21st of October 2016, multiple major DDoS attacks happened which took down numerous high-profile websites such as Netflix, Twitter, GitHub, Airbnb and others. This denial of service attack, known as the Mirai botnet attack, was a result of the Mirai malware installed on a large number of IoT devices. Such attacks illustrated the risks associated with poor security on IoT devices.
As the number of IoT devices continue to grow every year, Michael believes that IoT and security is going to continue being very much like oil and water. That’s partly because security is hard. IoT devices have a number of constraints:
- Actual device in terms of their CPU and/or microcontrollers and their ability to deal with cryptography
- Power constraints
- Lack of a trusted execution environment or secure element that allows the device to store keys in a secure manner
On the 1st of January 2020, Forbes reported that the state of California IoT Security Law came into effect mandated that all IoT devices sold in the state must also have “reasonable cybersecurity measures” embedded.
Another point that Michael highlighted in the podcast is the one regarding AI bias. This is a challenge that traditional insurers models are going to run into according to Michael. There has been an increase in statistic models and AI based systems for measuring different things. The problem that many of those algorithms that run statistical models or AIs are bias. There algorithms are completely opaque and there is no open source as they’re often considered as their organisation’s competitive advantage or secret sauce.
Self-Sovereign Identity and IoT white paper
In August 2020, the Sovrin Foundation published their Self-Sovereign Identity and IoT white paper.
The paper had two objectives:
- To make the SSI community aware of the opportunity that exists in the IoT space
- To make the IoT community aware of the potential and the possibilities that SSI, the DIDs and the credentials bring in addressing some of the security challenges that exist in IoT
The white paper uses three personas — Jamie, Bob, and Bessie the Cow —to provide a basic introduction to SSI and IoT, explore practical challenges in context, and describe how SSI in IoT can meet these challenges.
SSI-in-IoT-whitepaper_Sovrin-design
Persona – Jamie – machine to person
Jamie is a 55-year-old male who has Type 1 diabetes since childhood and has recently been diagnosed with early onset dementia. In recent years, he has been using a glucose meter implanted under his skin. The glucose meter connects to an App on his phone to keep a record of his glucose levels. Jamie has been sharing this data with his endocrinologist.
His challenges and his partner’s challenges are ensuring he gets his regular dose of insulin and the risk of him wandering away because of his dementia / Alzheimer.
With the use of decentralised identifiers and verifiable credentials, it is possible for his partner, Anne, to share delegated authorization to different people to have access to this information, such as access to the glucose meter. The other option, which is at a conceptual level, is to have inserts in Jamie’s shoes which can provide GPS location of where he is. These inserts can recognize Jamie by his gait and can even track Jamie’s physical location. This of course provides very personal information on Jamie.
Anne, being Jamie’s legal guardian can share delegate access to rescue services, both the location information coming from the insert, and potentially the glucose levels information. The aim is that this could lead to a faster and safe recovery of Jamie before he goes into an insulin shock.
Persona – Bob – machine to machine
Bob is a facilities manager in a financial office who is responsible for the infrastructure and keeping the bank’s staff, financial resources, confidential information and proprietary data safe. He has a lot of devices from heating, ventilation, security systems, network access for WIFI access points, area access and CCTV. It’s very labour intensive to set up, provision devices and to set them up on the network.
SSI along with DIDs and credentials provide the ability to automate to manage credentials for each of those devices whether is to replace them or revoke them for example.
DIDs and credentials provide Bob with a global means to establish the identity of IoT devices, people, and organisations. This enables him to standardise the management of both Machine To Machine interactions (e.g. CCTV cameras uploading their footage to a server) and Machine to Person interactions (e.g. doorways controlling entering and exiting of restricted areas).
The use of DIDs and VC’s in the asset management platform and wider IT ecosystem will increase security by ensuring all IoT devices are able to definitively self-identify and authenticate.
Persona – Bessie the cow – digital twins
Bessie is a Black Angus cow being raised by a rancher (keeper). The keeper (in contrast to the owner) of Bessie is required to keep records about Bessie, from birth to death. The tracking of cattle, and other farm animals, throughout their lives is a critical element in ensuring safety of the food supply chain. This was starkly proven during the foot-and-mouth outbreak occurred in 2007 in the UK when millions of animals were culled.
Today animals have a passport when they are born that tracks all of the animals’ movements. The challenge is that this comes as a physical piece of paper which creates a number of issues from being tampered, modified, and lost.
SSI brings the following elements to Bessie the cow and its ecosystem:
- Eliminates paper
- Managing multiple stakeholders
SSI brings an element of data quality issue when eliminating paper. Instead of having someone having to write information on a piece of paper or having to rekey something you can avoid spelling mistakes, typos and transcription errors by introducing SSI.
From a multiple stakeholders perspective, there have been issues or instances of where the person who has the cow on their property, along with the cow’s passport decides to sell the cow even if they don’t own it. SSi cryptographic credentials helps to introduce the notion of guardianship and delegation concept to avoid such type of problems.
Business value coming out of SSI solutions
SSI solutions bring two type of business values:
- Operational savings through reductions of liability and mitigation of risk. Another example are savings around data quality issues.
- When you start to have high confidence, high assurance, high trust around the interaction that you’re having, it starts to open the door for whole new business, different business models, new products and services to be created.
About the Sovrin Foundation and its work on IoT
The Sovrin Network- Making Self-Sovereign Identity a Reality from Sovrin Foundation on Vimeo.
The Sovrin Foundation is a 501 (c)(4) nonprofit organization established to administer the Governance Framework governing the Sovrin Network, a public service utility enabling self-sovereign identity on the internet. The Sovrin Foundation is an independent organization that is responsible for ensuring the Sovrin identity system is public and globally accessible.
Sovrin works alongside Decentralised Identity Foundation, and Trust Over IP Foundation to raise the profile of SSI in the IoT space.